Slow Get and Slow Post attacks are two types of cyber attacks that operate by gradually sending a large number of GET or POST requests to a targeted server, which can overload the server and slow down or even crash the website. In this article, we’ll explore the mechanics of these attacks, the risks they pose, and strategies for preventing and mitigating these threats.
What are Slow Get and Slow Post Attacks?
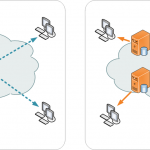
Slow Get and Slow Post attacks are types of DoS attacks that aim to overload a server by gradually sending large amounts of GET or POST requests to the targeted website. Slow Get attacks send GET requests to the server, while Slow Post attacks send POST requests.
In a Slow Get attack, the attacker sends GET requests to the server at a very slow pace, which can exhaust the server’s resources over time. Slow Post attacks work similarly, but instead of sending slow GET requests, the attacker sends slow POST requests to the server.
What are the Risks of Slow Get and Slow Post Attacks?
Slow Get and Slow Post attacks pose a significant risk to businesses and individuals, as they can cause websites to slow down or crash, leading to lost revenue, reputational damage, and decreased user engagement. Additionally, these attacks can be difficult to detect, as they often involve low-level activity over an extended period of time.
There are several types of slow attacks, including:
- Slow Read attack: This type of attack is a low and slow type of Denial of Service (DoS) attack where the attacker sends a large number of HTTP requests to a server and keeps them open for as long as possible. This causes the server to keep resources tied up and unable to serve other clients.
Tools used for Slowloris attacks include SlowHTTPTest, OWASP Slowloris HTTP DoS Tool, and R.U.D.Y (R U Dead Yet?) DoS Tool.
To mitigate Slowloris attacks, the following steps can be taken:
- Limit the number of connections that can be opened by an IP address.
- Set timeouts for HTTP connections to prevent them from staying open indefinitely.
- Implement a Web Application Firewall (WAF) to detect and block Slowloris attacks.
- Slow POST attack: This type of attack is similar to the Slowloris attack, but instead of sending HTTP requests, it sends large HTTP POST requests to the server. This causes the server to allocate resources to process the request, which can eventually cause it to crash.
Tools used for Slow POST attacks include OWASP’s SlowHTTPTest, HTTPDOS, and PyLoris.
How Can Organizations Protect Against Slow Get and Slow Post Attacks?
To protect against Slow Get and Slow Post attacks, organizations can take proactive measures such as:
- Implementing rate-limiting measures on their web servers to limit the number of requests that can be sent by any given IP address.
- Deploying a Web Application Firewall (WAF) to filter out malicious traffic and block suspicious requests.
- Monitoring server performance and usage levels to identify unusual spikes in traffic or activity.
- Keeping software and systems up to date with the latest security patches and updates to mitigate the risk of known vulnerabilities being exploited.
- Conducting regular security audits and penetration testing to identify potential weaknesses in web applications and networks.
Conclusion
Slow Get and Slow Post attacks are a growing threat to organizations and individuals, as they can cause significant disruption and damage to websites and online services. By implementing a proactive and layered approach to cybersecurity, organizations can protect themselves against these threats and mitigate the risks posed by Slow Get and Slow Post attacks.